
“Agent Smith”: The New Virus to Hit Mobile Devices In India
Check Point Researchers recently discovered a new variant of mobile malware that quietly infected around 25 million devices, while the user remains completely unaware. The primary targets, so far, are based in India though other Asian countries such as Pakistan and Bangladesh are also affected and are even successfully penetrated into noticeable number of devices in developed countries such as Saudi Arabia, UK and US.
Disguised as Google related app, the core part of malware exploits various known Android vulnerabilities and automatically replaces installed apps on the device with malicious versions without the user’s interaction. This unique on-device, just-in-time (JIT) approach inspired researchers to dub this malware as “Agent Smith”.
“Agent Smith” currently uses its broad access to the device’s resources to show fraudulent ads for financial gain. This activity resembles previous campaigns such as Gooligan, HummingBad and CopyCat. However, it could easily be used for far more intrusive and harmful purposes such as banking credential theft. Indeed, due to its ability to hide it’s icon from the launcher and impersonates any popular existing apps on a device, there are endless possibilities for this sort of malware to harm a user’s device.
How Does It Work?
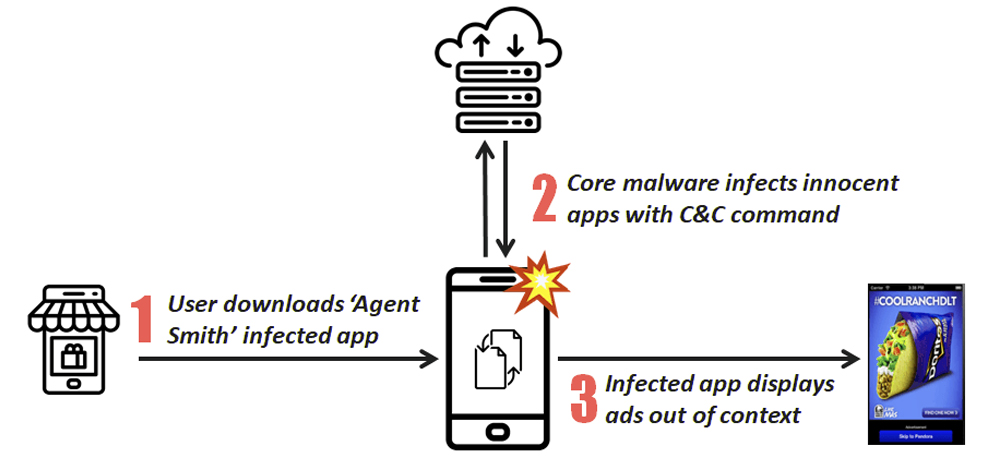
Agent Smith” has primarily three phases in its attack flow.
- A dropper app lures victim to install itself voluntarily. The initial dropper has a weaponized Feng Shui Bundle as encrypted asset files. Dropper variants are usually barely functioning photo utility, games, or sex related apps.
- The dropper automatically decrypts and installs its core malware APK which later conducts malicious patching and app updates. The core malware is usually disguised as Google Updater, Google Update for U or “com.google.vending”. The core malware’s icon is hidden.
- The core malware extracts the device’s installed app list. If it finds apps on its prey list (hard-coded or sent from C&C server), it will extract the base APK of the target innocent app on the device, patch the APK with malicious ads modules, install the APK back and replace the original one as if it is an update.
With the main purpose of spreading the infection, “Agent Smith” implements in the “core” module:
- A series of ‘Bundle’ vulnerabilities, which is used to install applications without the victim’s awareness.
- The Janus vulnerability, which allows the actor to replace any application with an infected version.
Steps to be followed to remove the malicious apps if you have been infected:
For Android:
- Go to Settings Menu
- Click on Apps or Application Manager
- Scroll to the suspected app and uninstall it.
- If it can’t be found then remove all recently installed apps.
For Android:
- Go to Settings Menu
- Scroll to ‘Safari’
- On the list of options, ensure that ‘block pop-ups’ is selected.
- Then go to ‘Advanced’ -> ‘Website Data’.
- For any unrecognized sites listed, delete this site.
The “Agent Smith” campaign serves as a sharp reminder that effort from system developers alone is not enough to build a secure Android eco-system. It requires attention and action from system developers, device manufacturers, app developers, and users, so that vulnerability fixes are patched, distributed, adopted and installed in time.
It is also another example for why organizations and consumers alike should have an advanced mobile threat prevention solution installed on the device to protect themselves against the possibility of unknowingly installing malicious apps, even from trusted app stores.
Check Point Researchers has submitted data to Google and law enforcement units to facilitate further investigation. As a result, information related to the malicious actor is tentatively redacted in this publication. Check Point has worked closely with Google and at the time of publishing, no malicious apps remain on the Play Store.