Experts agree that misinformation surrounding the coronavirus poses a threat to human health.....
Microsoft today released security updates to fix a total of 115 new security vulnerabilities in various.....
We naturally tend to be more relaxed at home, especially when it comes to security. After all, we’re in the safety.....
Misinformation pertaining to the coronavirus is proliferating and circulating through pockets of society.....
Your Gmail account is a repository of your online purchasing history, your passwords and other personal information.....
This year, tax firms are facing intimidating malware threats. “If you have the word ‘tax’ in your domain name.....
Android platform has stayed true to its commitment to provide open and free source code. The source code.....
A popular WordPress theme plugin with over 200,000 active installations contains a severe but easy-to-exploit.....
The World Health Organization (WHO) has released a warning about Coronavirus-themed phishing attacks.....
In digital marketing and online advertising, Spamdexing or SEO spam is one of the most common hacks to increase.....
Finding a user’s location can be one of the most powerful tools for digital marketers. However, factors such.....
Intel has warned of a critical vulnerability in the CSME security engine and has urged users to apply.....
Adobe today released the latest security updates for five of its widely used software that patch a total.....
Zero-day attacks come without warning. Such attacks can pose a high risk for a company or business if appropriate.....
Researchers have reported a vulnerability in WhatsApp desktop client for iPhones which puts victim's.....
A new utility tool called EmoCheck has been released by Japan CERT. It will allow Windows users to easily check.....
Researchers has found another significant vulnerability in sudo utility that under a specific configuration.....
Cybersecurity researchers disclosed details of two recently patched potentially dangerous vulnerabilities in Microsoft Azure.....
At the Geospatial World Forum 2020 session on ‘Geo4SDGs’, light will be shed on the way geospatial and 5G together.....
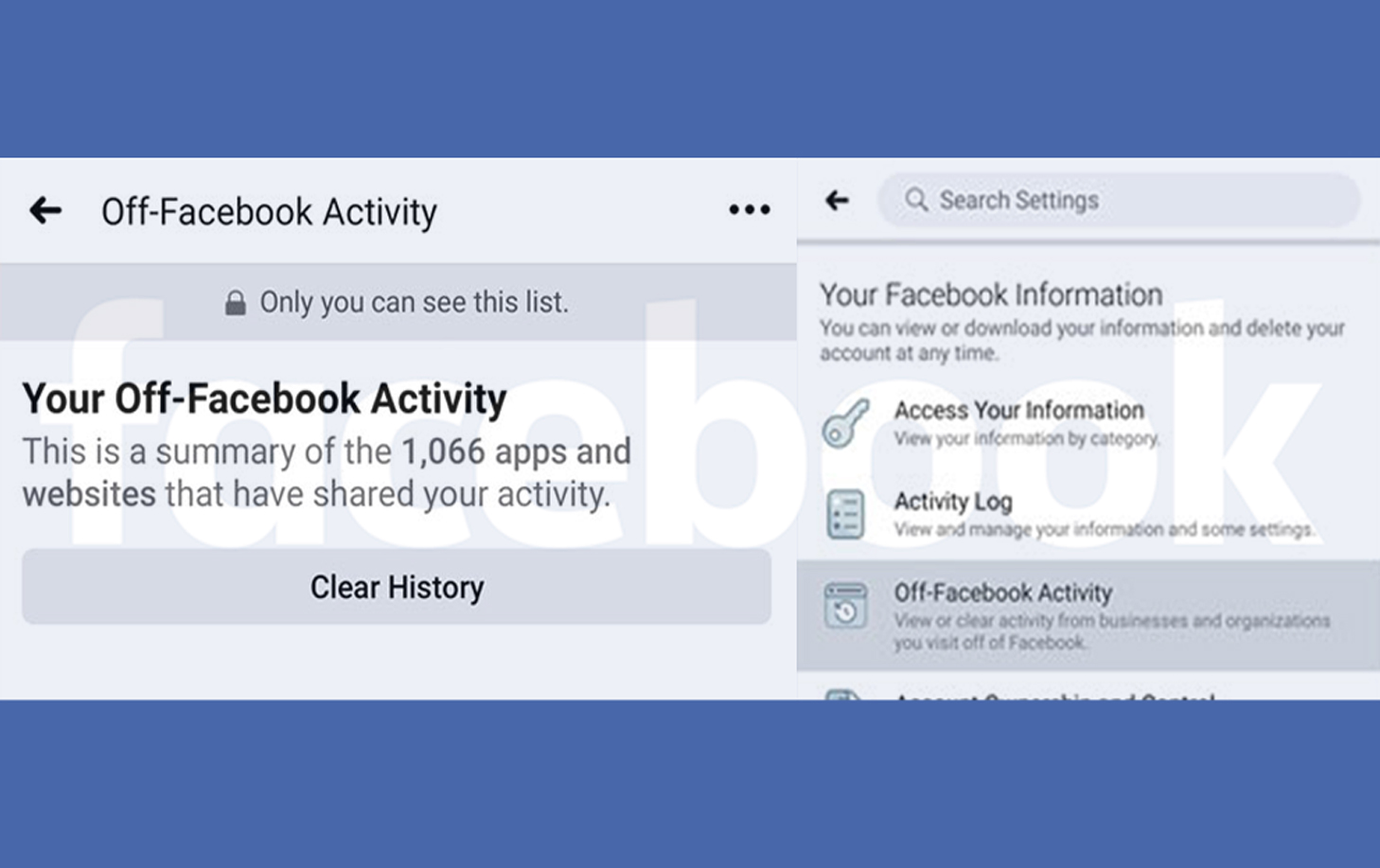
Facebook is one of the world's biggest advertising platforms, and that's because it knows a lot about you, me, and everyone.....
For the third time in less than a year, Intel has disclosed a new set of vulnerabilities related to the speculative.....
Recently, scammers impersonating representatives from Amazon were reported calling up Amazon users and offering.....
Solar development is an incredibly fast-growing industry. The solar industry has seen 50% growth year-over-year.....
A group of researchers reported that FTCode ransomware is now armed with browser, email password-stealing.....
After thoroughly having its secrets laid bare last month in a Microsoft exposé report, the operators.....
Juice jacking is becoming a real threat for people, especially for those charging their phones.....
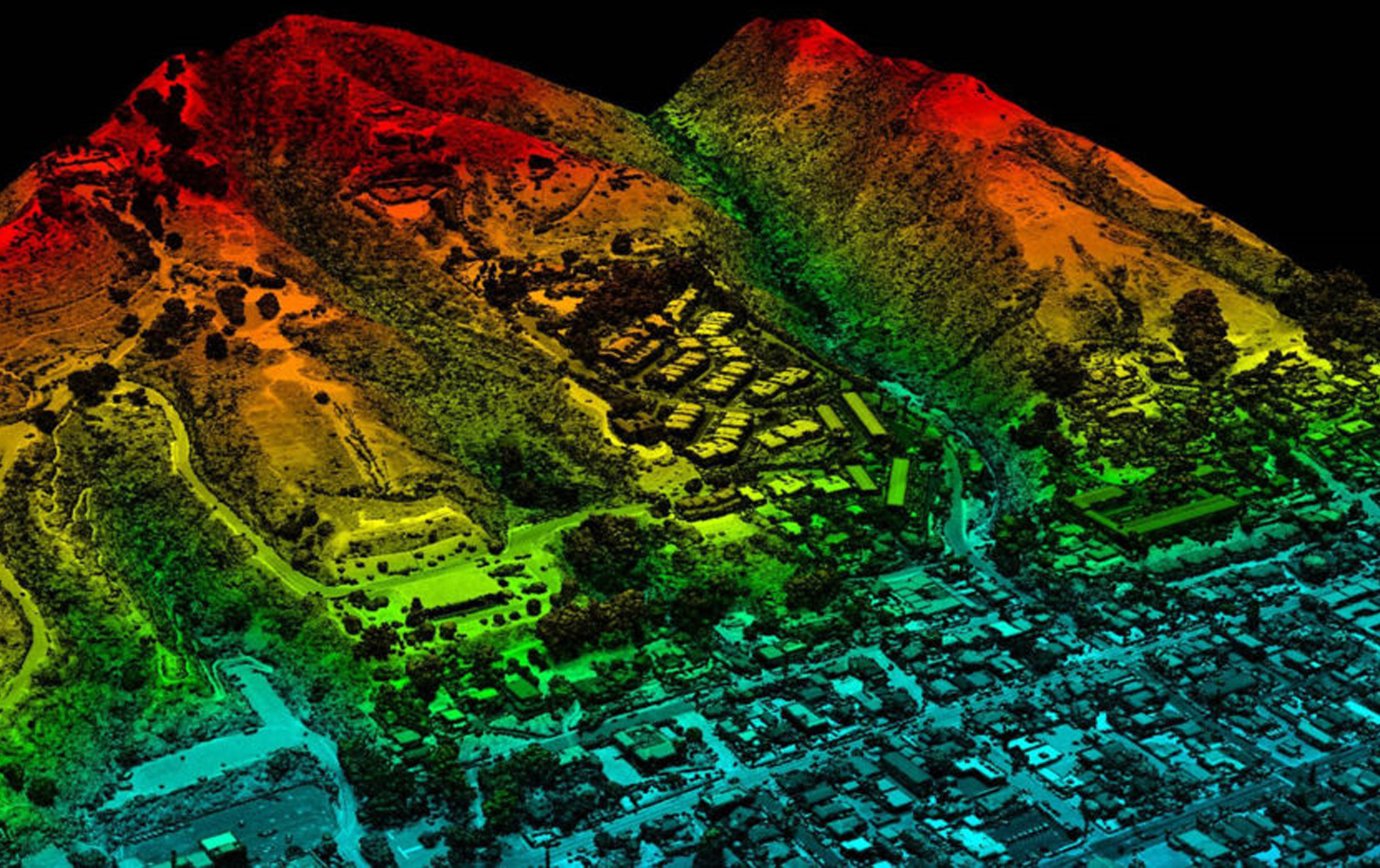
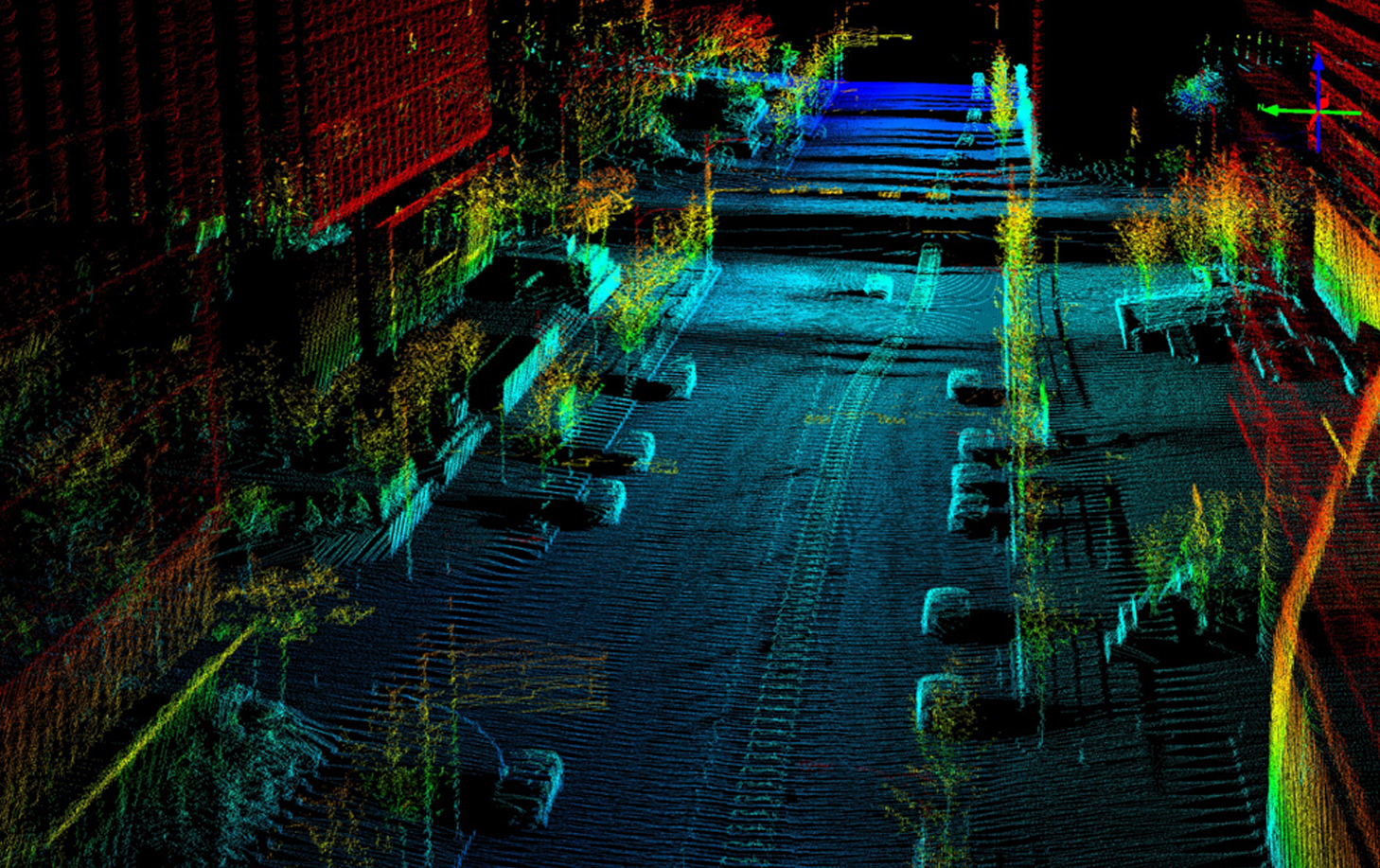
LiDAR can be used to generate detailed maps of topography and retrieve digital elevation data.....
Google Project Zero security researchers have published technical details on the critical iMessage vulnerability.....
Security experts have detected that attackers are leveraging a new and unique evasion technique to launch phishing attacks.....
WordPress is a well-known open-source content management system (CMS) used for creating websites and personal blogs. Given the wide usage of the platform.....
TikTok, the 3rd most downloaded app in 2019, is under intense scrutiny over users' privacy, censoring politically controversial content.....
Despite the formidable capabilities of cyber security tools, including their abilities to behave in hyper-fast, extremely dynamic, and exceedingly.....
Steganography has long been used by malware authors to hide malicious data within legitimate-looking images and currently, it is being used by cybercriminals.....
Geolocation platforms and apps have proven to be more than merely handy tools used in sales. They provide amazing insight into any kind of target.....
Nearly 45 new vulnerabilities get discovered on average every day. Since 2016, Researchers has observed an increase of 130% in the total.....
Plugging an unattended USB flash drive to a host system or network is no less than a threat. Such drives can be infected with viruses.....
Recently, more than a dozen entrepreneurs’ accounts were hacked via the Telegram messaging app. The hack suggests a possible interception.....
LIDAR has multiple applications and utilities and their full scope would soon extend beyond our imagination as it unravels in the future.....
5G will impact key sectors like manufacturing to energy, transportation, smart cities, healthcare and much more. Its improved speeds.....
WhatsApp may be one of the most popular messaging apps, but it has had its share of security issues. Security research group Check Point Research announced.....
When it comes to creating long, secure passwords for accounts, computer users frequently fancy themselves too busy to bother, and unable to.....
Cybercriminals have developed a new ransomware variant called Zeppelin. It is being used to target healthcare and tech companies in U.S., Canada, and Europe.....
Previously, bank heists involved snatching the cash and running. Now, they’re digital, more elaborate, and more dangerous. Over the past five years.....
Adobe released updates for four of its widely used software—including Adobe Acrobat and Reader, Photoshop CC, ColdFusion, and Brackets—to patch.....
Social media companies have been searching for better ways to identify, and remove harmful online content. Human moderation of social media.....
The now ubiquitous QR code (machine readable optical labels that are arranged as squares with black designs in them) for phones are being.....
A team of cybersecurity researchers has disclosed a new severe vulnerability affecting most Linux and Unix-like operating systems, including FreeBSD.....
Leaving a vulnerable system unpatched can invite troubles for an organization. The issue can turn worse when the organization suffers a cyberattack.....
A DoS flaw tracked as CVE-2019-2232 is said to be the most severe flaw this particular update tends to. The fix has been rolled out for Android.....
Cyber attacks continue to evolve at an ever-increasing pace. Threats have become more sophisticated and dangerous compared to just a few years ago.....
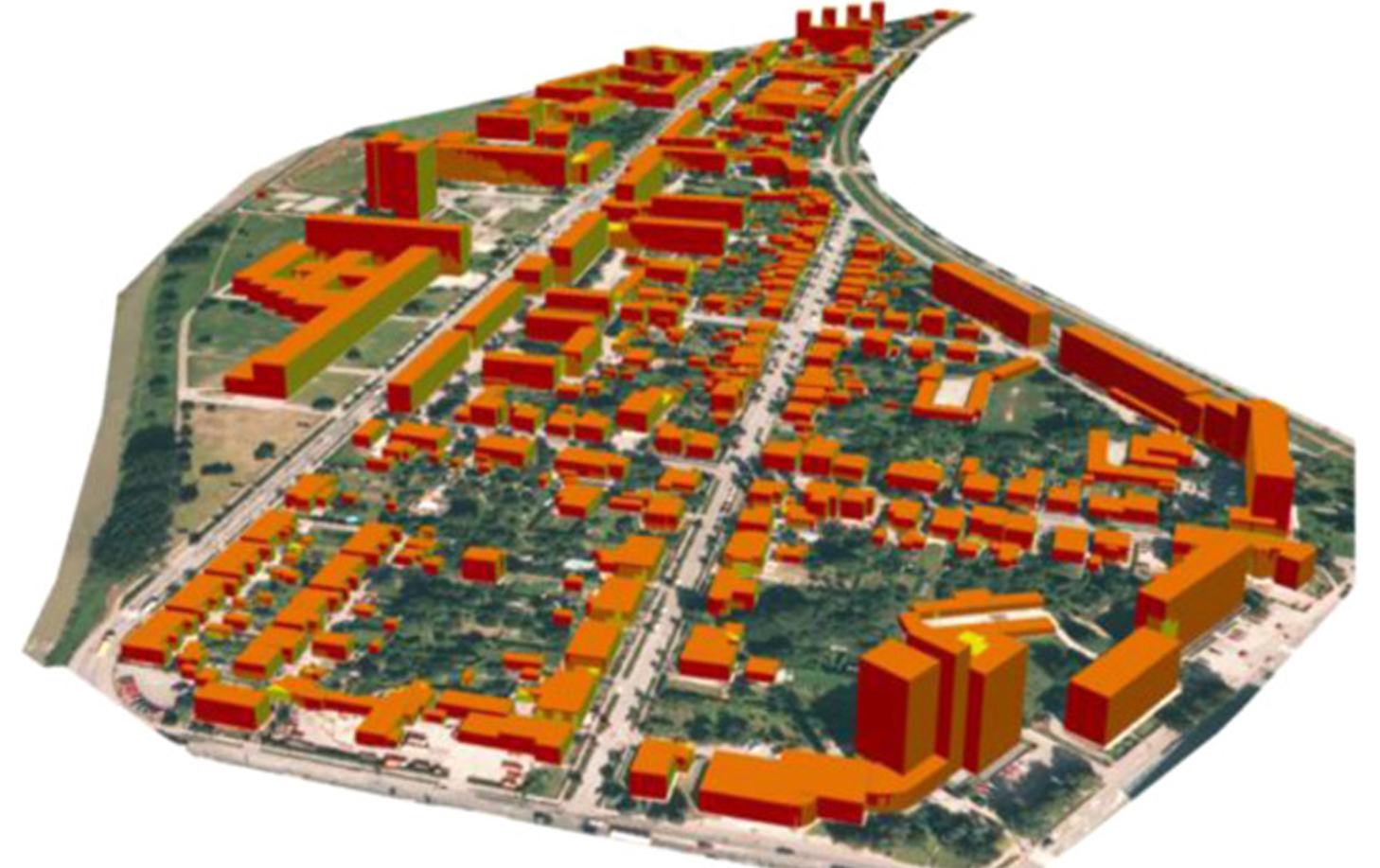
With the increasing population and mass urbanization along with pressure of modernization on developing countries, the construction.....
Most mobile users understandably worry about known vulnerabilities in the core operating system of their devices, which can give an attacker.....
When it comes to the relationship between business development and technological innovation, we can generally separate two schools of thought.....
Hostile cyber threats are escalating in frequency and severity, and threaten to undermine our civil and commercial institutions.....
Biometric passwords have become popular, but vulnerabilities in these systems leave users’ phones and data at risk of being hacked.....
Working with public cloud infrastructure without the right understanding of risks and security challenges may prove to be a risky bet today.....
Researchers recently announced that they discovered a means of taking over Apple’s Siri, Google Home, or Amazon’s Alexa from hundreds.....
Microsoft has a released an optional Windows 7 and Windows Server 2008 R2 SP1 update that let's customers who have signed up for extended.....
Scanning QR codes for authentication lets you log in to an app without having to memorize credentials. Chat applications, banking services.....
A smartphone identifies its position via either satellite radio signals or GNSS (Global Navigation Satellite System). Currently, the vast majority.....
There has been a steep rise in ransomware attacks against multiple government organizations, and cities across the globe. Hackers are.....
Google last update to its Chrome browser for Windows, Mac and Linux desktop environments, fixing two high-level vulnerabilities.....
Global Navigation Satellite System, popularly known as GNSS, is a satellite navigation or satnav system that uses small satellites.....
Researchers discovered the Dtrack spy tool when they were analyzing the ATMDtrack malware that was targeting Indian banks.....
Over the past few months, hundreds of Android users have been complaining online of a new piece of mysterious malware that hides.....
IoT is continuously making progress to our homes and as more IoT devices are getting released on a regular basis, it can help to track.....
Cash App payment service conducts marketing campaigns that offer cash rewards, on social media platforms such as Twitter or Instagram.....
A new ransomware dubbed MedusaLocker has been observed to be infecting victims from all over the world. Details such as mode of distribution.....
Cybersecurity researchers claim to have discovered a previously undocumented backdoor specifically designed for Microsoft SQL servers.....
The study further found that 63% of Indian businesses were concerned about being exposed to cyber criminals due to employee error.....
A new type of malvertising campaign that leverages Google ads has been found distributing malware. One such incident has been cited.....
Building information modeling (BIM) is a process involving the generation and management of digital representations of physical and.....
Digital fraudsters are using compromised servers and bogus links in an ongoing effort to target LinkedIn members with scams.....
Adobe issued an out of band updated today for Experience Manager, Experience Manager Forms, Adobe Acrobat and Reader and Download Manager.....
With data being the ‘new oil’ and the debates on privacy occupying the center stage of social and political discourse, it is time.....
Bluetooth is a wireless communication protocol developed in 1998. It simplifies the transfer of files, photos and docs for low peripheral.....
In real estate, there is a saying about what matters most: location, location, location. This is also true for other business.....
The tool has been introduced following the rise in fake Instagram emails. The new feature introduced by Instagram aims to verify emails.....
Travelers, especially those on business trips carry devices with valuable personal and business information making them lucrative.....
Security experts disclosed a remote code execution vulnerability tracked as CVE-2019-16920. The vulnerability is an unauthenticated.....
As an increasing number of companies offer the option of working remotely, cybersecurity is an important aspect to consider.....
A new and actively distributed malware strain dubbed Masad Stealer steals files, browser information, and cryptocurrency wallet data.....
Geolocation technology is becoming a mainstay in society after being utilized from navigation tools to social media platforms.....
Google has removed two malicious ad blockers from its Chrome Web Store after a researcher discovered they were carrying out ad fraud.....
D-Link DNS-320 ShareCenter network-attached storage (NAS) devices are affected by a critical vulnerability that can be exploited.....
Social media sites such as Facebook, Instagram, Twitter and the rest are fun ways to keep in touch with friends and family.....
Google has released an urgent software update for its Chrome web browser and is urging Windows, Mac, and Linux users to upgrade.....
Cybersecurity researchers recently published details and proof-of-concept for an unpatched zero-day vulnerability in phpMyAdmin—one.....
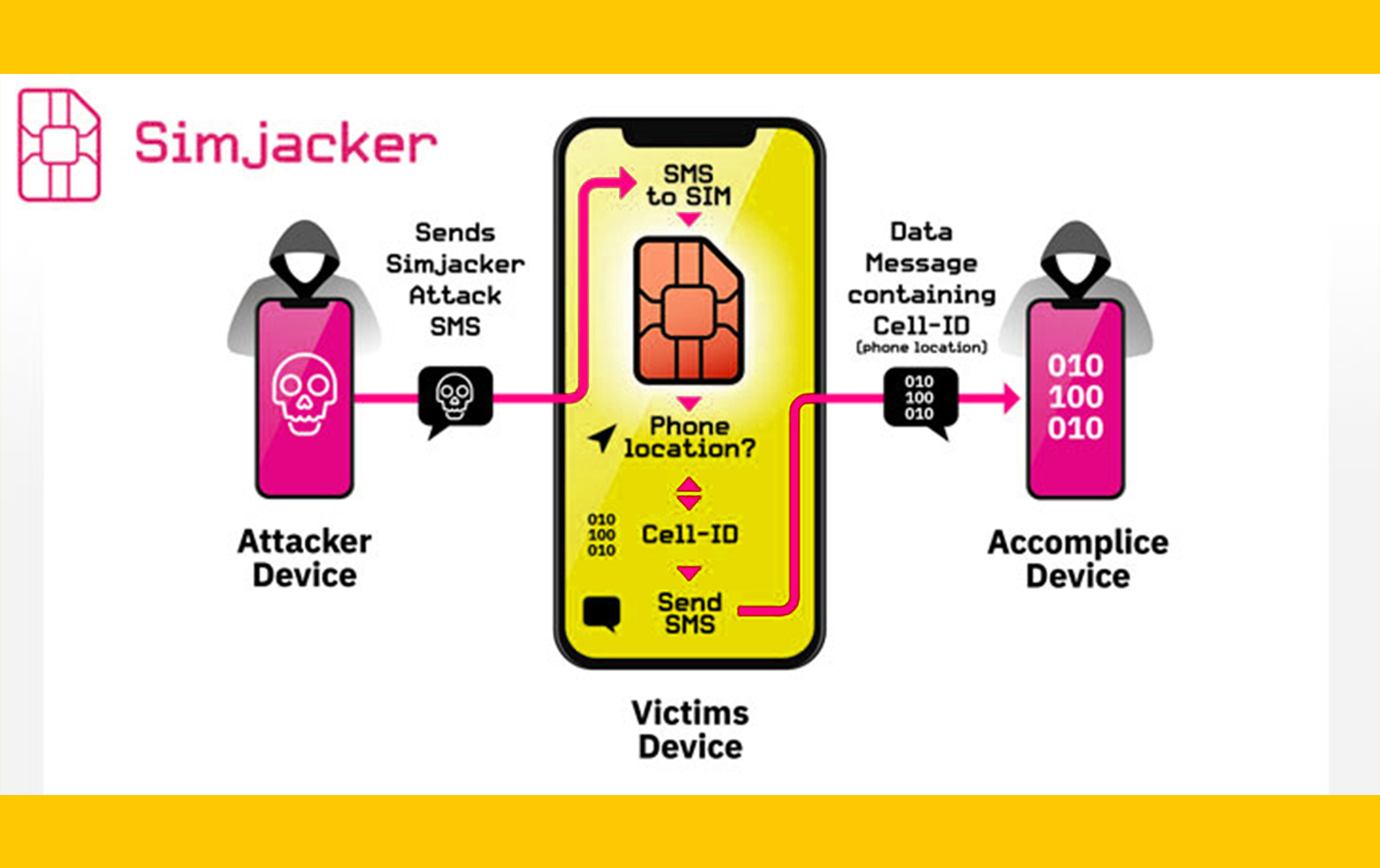
Cybersecurity researchers today revealed the existence of a new and previously undetected critical vulnerability in SIM cards.....
Cybersecurity researchers today revealed the existence of a new and previously undetected critical vulnerability in SIM cards.....
Check Point researchers recently discovered a vulnerability to advanced phishing attacks in a wide variety of Android phones.....
Foxit Software is forcing its customers to reset their passwords in response to an unauthorized party gaining access to user accounts.....
Google has updated Chrome to fix a high-severity flaw that could enable hackers to carry out remote code execution (RCE) attacks.....
Apple released iOS 12.4.1 to fix a critical jailbreak vulnerability, like it or not, that was initially patched by the company.....
Beware! Attackers can remotely hijack your Android device and steal data stored on it, if you are using free version of CamScanner.....
Traditionally, within the electric utilities, GIS has primarily been a tool for asset managers to access basic information about.....
Epic Games, the creator of the popular 'Fortnite' video game, is facing a class-action lawsuit from gamers.....
The threat of ransomware is becoming more prevalent and severe as attackers' focus has now moved beyond computers.....
New vulnerabilities found in messaging app WhatsApp can be used by hackers to manipulate and intercept messages.....
Earlier this year, we published our research on the Reverse RDP Attack. In our previous blog post, we described.....
Cities are increasingly seen not just as the engines of innovation and economic growth but also as the epicenter.....
Google's cybersecurity researchers have finally disclosed details and proof-of-concept exploits for 4 out of 5 security.....
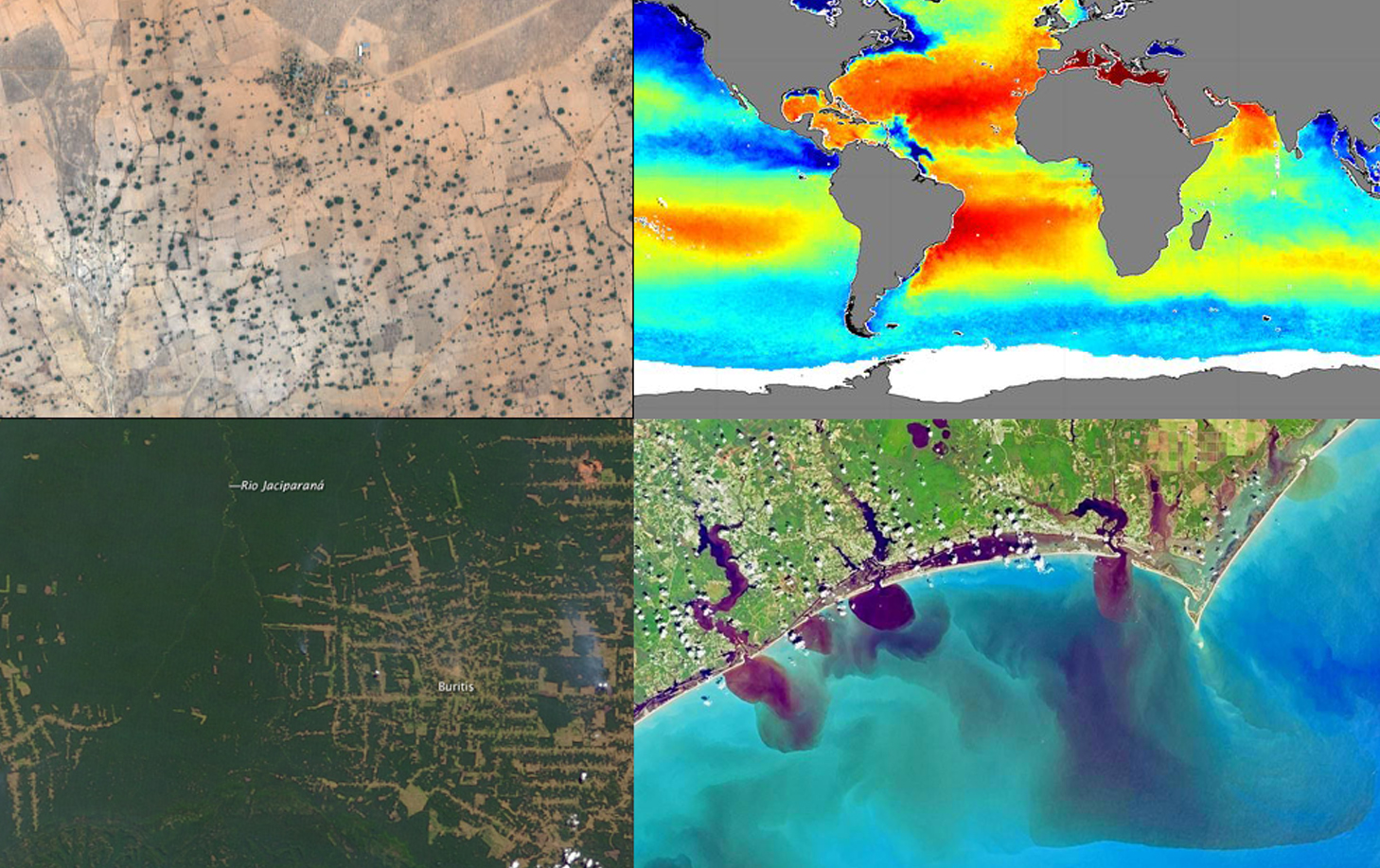
We are living in an era of environmental uncertainty. One the one hand the eastern and north-eastern Indian states.....
You should be more careful while playing a video on your smartphone—downloaded anywhere from the Internet or received through email.....
Facebook has opened up its Map With AI service to the OSM community. This means anyone can have access to Facebook’s....
A new research by Symantec talks about the dangers of Media File Jacking, a type of attack undertaken by cybercriminals....
Check Point Researchers recently discovered a new variant of mobile malware that quietly infected around 25 million devices,....
The explosion of technology has led to a rapid rise in digital assets and transactions. Mobile phones are now....
Today, digital assets and transactions rapidly rised by the gwroth of advanced technolgy. social media platforms....
Microsoft today released an updated version of its "Outlook for Android" that patches an important security vulnerability....
All of that sounds daunting—like cybersecurity is an exercise in futility—but there are things you can do....
In today’s busy, high-tech world, most of us have a wide variety of our own personal information stored either online...
Whatsapp has recently patched a severe vulnerability that was being exploited by attackers to remotely install surveillance...
Microsoft released the source code of a new Windows Terminal application today featuring multi-tab support...
Parrot 4.6 released by Parrot security with so many updates that bring all the hacking tools on the table with new futures...
The Retefe banking Trojan resurfaces in that threat landscape and implements new techniques to avoid detection...
Docker Hub, one of the largest cloud-based library of Docker container images, has suffered a data breach after an unknown...
Several video game companies have been found to be infected with malware in a similar manner as was done with ASUS computers...
The cybercriminal group behind the infamous DNSpionage malware campaign has been found running a new sophisticated...
After Google began restricting which Android apps can gain SMS and Call Log permissions, the company is now focusing on...
A new phishing scam called the "The Nasty List" is sweeping through Instagram and is targeting victim's login credentials...
Microsoft has started notifying some Outlook.com users that a hacker was able to access accounts for months earlier this year...
Android device owners are complaining about a bug in Skype that makes it automatically answer incoming calls....
The Australian Cyber Security Centre (ACSC) is warning Aussies about malicious emails from scammers pretending...
IoT devices make our lives easier. Smart home technology, for example, can help users improve energy efficiency...
A popular family tracking app, Family Locator, was found leaking the real-time locations of more than ...
In the latest research, A four-person research team from the Korean Advanced Institute of Science and Technology...
Microsoft Thursday announced that the company is bringing its anti-malware software to Apple’s macOS operating system...
Location is at the very core of smartphone experience for Android users. Be it searching a good eatery or a store...
A new variant of the Monero mining malware has been detected by the Sand Blast Agent Forensics team, which is spreading...
A new ransomware called JNEC.a spreads through an exploit for the recently reported code execution ACE vulnerability in WinRAR.
Microsoft released its March 2019 software updates to address a total of 64 CVE-listed security vulnerabilities...
LokiBot is an info-stealer malware that was first detected in February 2016. LokiBot targets Android systems...
Unmanned aerial systems (UAS), more commonly known as drones, have infiltrated the geospatial world. And that’s a good thing...
You must update your Google Chrome immediately to the latest version of the web browsing application...
3D digital models derived from high-resolution aerial photography are helping network operators plan the rollout of services...
The International hedge funds have become a victim of a new phishing campaign called "Beyond the Grave" that alter data...
A new malware has been spotted by security firm Malwarebytes, which is making rounds in the e-commerce space...
During the last few decades, congestion has become a major challenge in Indian Cities. Not only in India but cities across the world face...
Smart devices, like security cameras, baby monitors, TV media boxes, smart TVs, printers, and gaming consoles,...
Symantec’s 2019 Internet Security Threat Report takes a deep dive into insights...
A new trojan named Muncy, a phishing campaign from DHL and entitled “DHL Shipment Notification” has been found targeting users worldwide.
Kali Linux 2019.1 released with a number of bug fixes and includes kernel up to...
An ongoing phishing campaign is using a new variant of Separ malware to infect hundreds of businesses located mainly in Southeast Asia...
JD Finance, a financial services arm of JD.com apologized to its users for storing screenshots without user permission after a user posted a video on...
Google Chrome's Incognito mode is a helpful feature for private browsing however, it is not free of any faults.
A new shocking report revealed that almost 620 million online account data from 16 famous websites are on sale on the dark web.