
Microsoft discovers new sLoad 2.0 (Starslord) malware
After thoroughly having its secrets laid bare last month in a Microsoft exposé report, the operators of the sLoad malware have put into circulation a revamped 2.0 version earlier this month.
This new sLoad version (also known as Starslord) doesn't change much, but the fact that the sLoad gang shipped a new version in less than a month after having its operations exposed shows the speed at which malware authors often operate.
THE SLOAD MALWARE OPERATION
The sLoad malware is not something new. It's a malware strain that has been around for years. The malware is what someone would call a "malware downloader" or "malware dropper."
sLoad's main purpose is to infect Windows PCs, gather information about the system they infected, send this info to a command and control (C&C) server, and then wait for instructions to download and install a second malware payload.
The malware exists to serve as a delivery system for more potent malware strains and to help the sLoad gang make money by providing pay-per-install space for other cybercriminal operations. Malware downloaders like sLoad are a dime a dozen. However, according to Microsoft, sLoad was one of the few malware downloaders that stood out due to an unneeded level of sophistication and its use of non-standard techniques.
SLOAD'S BITS OBSESSION
According to a Microsoft report from December 2019, sLoad had become one of the few malware strains that ported its entire host-server communications systems to the Windows BITS service. For those unfamiliar with the term, Windows BITS is the default system through which Microsoft sends Windows updates to users all over the world. The BITS service works by detecting when the user is not using their network connection and utilizing this downtime to download Windows updates.
But the BITS service is not entirely reserved for the Windows Update process. Other apps can tap into BITS and use it to schedule tasks and network operations to take place when the computer's network connection goes idle. The sLoad authors appear to be some of the biggest fans of this service. Microsoft says that the malware's entire network stack was configured to work via the Windows BITS service of an infected host.
The malware would set up BITS scheduled tasks that would execute at regular intervals. These tasks would be used to talk with its C&C server, download secondary malware payloads, and even send data from an infected host back to the C&C server (sLoad v1.0 included an ability to take screenshots of an infected host). While other malware -- like Win32/StealthFalcon, Zlob.Q, UBoat RAT, Rustock, and Linkoptimizer -- also used BITS, sLoad relied on it for almost all communications, making it an unique entry on the malware landscape.
Furthermore, besides using silent BITS communications, sLoad also heavily relied on the PowerShell scripting language, which it used to support a "fileless execution" mode where it ran completely inside the RAM, without placing artifacts on disk.
A NEED TO CHANGE MODUS OPERANDI
Microsoft's report from last month exposed sLoad's capabilities and increased awareness among cyber-security vendors about the malware's modus operandi. Exposés like these are dangerous for malware gangs, as they could mean their malicious payloads get detected more often. In most cases, most malware gangs upgrade or re-tool operations, hoping to stay a step ahead of cyber-security vendors. The sLoad gang did exactly this. Within a few weeks, they revamped their code and change things around, shipping out a new sLoad v2.0 starting this year.
However, if the sLoad gang was hoping to stay one step ahead of Microsoft, they didn't succeed, as the company published another exposé today detailing the new v2.0 in a similar depth as v1.0 last month. According to Sujit Magar, a malware analyst part of the Microsoft Defender ATP Research Team, sLoad 2.0 has largely remained the same, still using BITS exclusively for all network operations, still relying on PowerShell scripts for fileless execution, and still working as a malware downloader for other criminal groups.
The only things that changed was the use of WSF scripts instead of VB scripts during the infection process, the addition of checks to detect if malware analysts are looking at the code, and the rollout of a new system that tracks the stages of an sLoad infection.
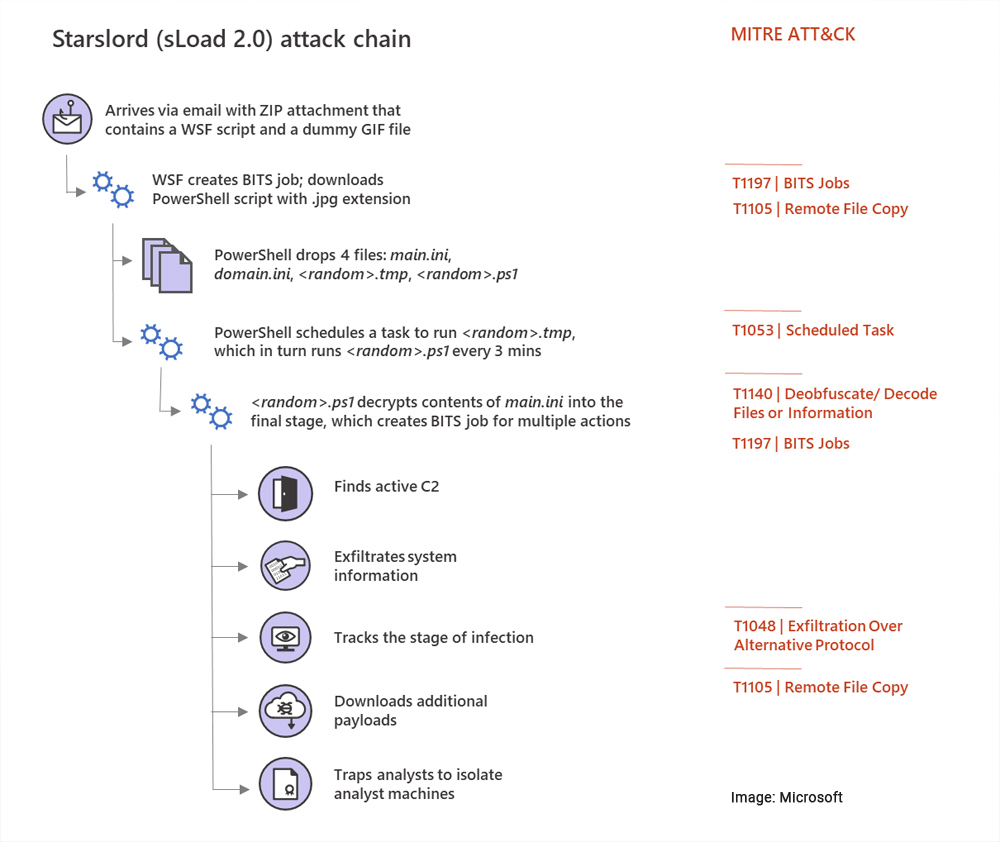
Of these three new additions, the last is the most novel one, not seen in other malware strains. This new mechanism works by adding a small numerical value at the end of a BITS job that communicates with the C&C server. The numerical value tells the sLoad team the stage of an sLoad infection. The purpose of this feature can vary. Magar believes this could be used to organize sLoad hosts into sub-groups, and then send commands to specific sLoad-infected hosts.
Another purpose could be that this feature was added for debugging purposes, in case new sLoad version crash or stop at a particular stage, allowing the sLoad team to send commands to the crashed sLoad infections and repair any bugs. Either way, Microsoft seems to be on top of the recent sLoad updates, and its latest technical report should help other vendors keep up with detecting this new version as well.